In my previous scripting tutorials, I've covered BASH, Perl and PowerShell scripting, and along the way, we built our own network port scanner using Perl. Here we will begin looking at the most widely used scripting language for hackers, Python.
Python has some important features that make it particularly useful for hacking, but probably most importantly, it has some pre-built libraries that provide some powerful functionality. Python ships with over 1,000 modules and many more are available in various other repositories. This isn't to say that scripting languages like BASH, Perl, and Ruby can't do the same things as Python, but building those capabilities are much easier using Python.
Adding Python Modules
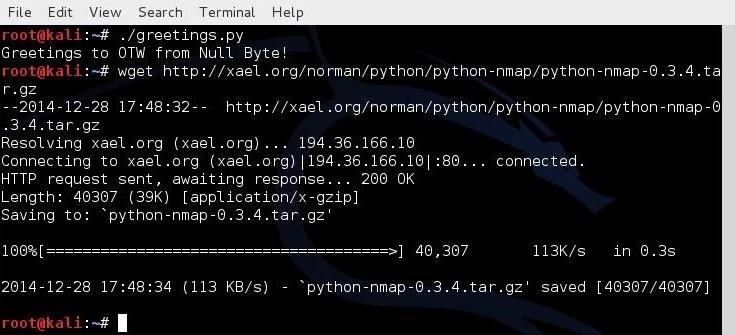
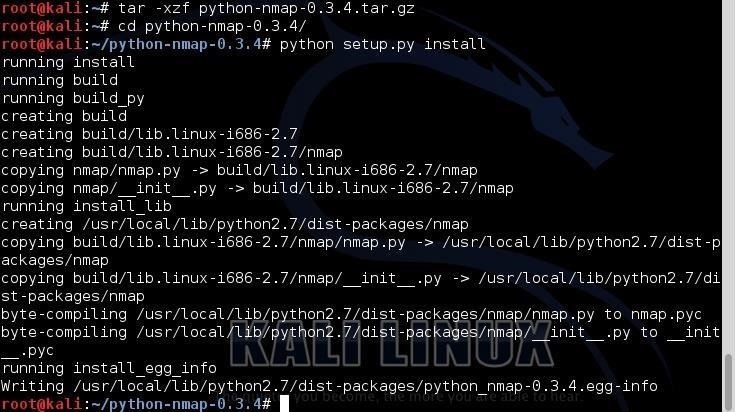
The Python standard library and modules provide an extensive range of capabilities including built-in data types, exception handling, numeric and math modules, file handling, cryptographic services, Internet data handling, and interaction with Internet protocols (IPs).If we need to install a third-party module, we can simply use wget to download it from the repository, uncompress the module, then run the python setup.py install command. As an example, let's download and install the Nmap python module from a small repository at xael.org.
After we have downloaded the new module, we need to uncompress it with tar:
kali > tar -xzf python-nmap-0.3.4.tar.gz
kali > cd python-nmap-.03.4/
Finally, we need to install the new module by typing:
Getting Started Scripting with Python
Now that know how to install modules in Python, I want to cover some of the basic concepts and terminology of Python, then the basic syntax, and finally, we will write some scripts that will be useful to hackers everywhere, which will demonstrate the power of Python.Like the other scripting languages we have explored, we can create our script in any text editor. I'll be using the built-in GUI text editor in Kali, Leafpad, but you can use whichever text editor you prefer.
Formatting
Unlike some of the other scripting languages, formatting is very important in Python. The Python interpreter uses the formatting to determine how code is grouped together. The particulars of the formatting are less important than being consistent. So, if you have a group of code that you start with double indentation, you must be consistent with the double indentation for Python to recognize that the code belongs together. This is different from scripting in other programming languages where formatting is optional and best practice, but not required.Running Python Files
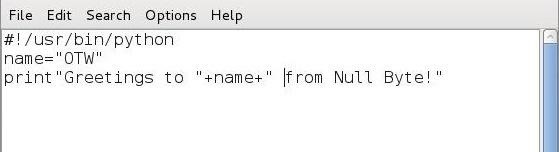
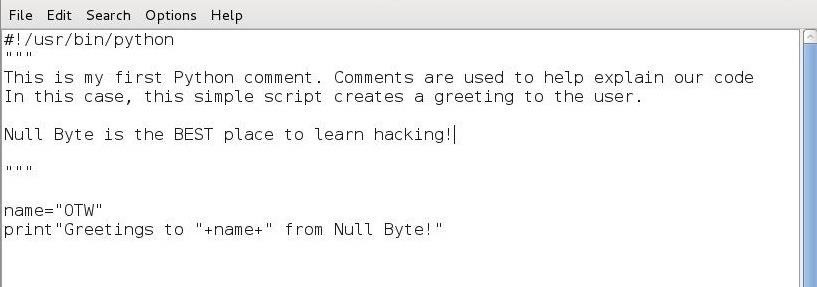
To become familiar with the basics of running Python files, let's create a simple script in Leafpad and save it as greetings.py.name="<your name>'
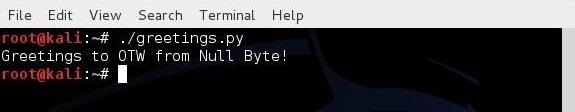
print "Greetings to " + name + " from Null Byte!"
Now, before we can run this script, we need to give ourselves permission to execute it. We need the chmod command to do that. (For more information on Linux permissions, see this article.)
kali > chmod 755 greetings.py
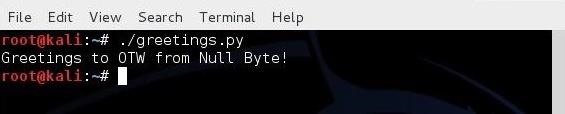
When we run this simple script, we get:
Comments
Like any programming and scripting language, Python has the capability of adding comments. Comments are simply words, sentences, and even paragraphs that explain what the code is meant to do. Although comments are not required, it sure is helpful when you come back to it two years later and can't remember what that script was meant to do.As you can see in the screenshot below, I have added a short multi-line comment to our simple greeting.py script.
Modules
Python allows us to group our code into modules. If we want to use a module, we need to "import" it. When we import a module, we then gain access to all of the classes, class methods, and functions (don't worry if you don't understand this. I'll try to explain it in my next tutorial on Python) that were created in the module. These modules are one of the key features that makes Python so powerful for the hacker.These are the very basics of the Python scripting language. In our second guide on Python scripting, we will add variables, lists, arguments, dictionaries, control statements, functions, and exception handling working towards developing some simple, but valuable hacking scripts, so keep coming back, my greenhorn hacker!
No comments:
Post a Comment